Secure Socket Layer (SSL) is a security protocol that was developed by Netscape Communications Corporation, along with RSA Data Security, Inc. The Primary goal of the SSL protocol is to provide a private channel between communicating applications, which ensures privacy of data, authentication of the partners, and integrity. The Secure Socket Layer (SSL) technology was used for the websites or web applications which need more security.
| SSL handshake protocol with two way authentication with certificates. (Photo credit: Wikipedia) |
Secure Socket Layer (SSL) is composed of two layers:
- At the lower layer, a protocol for transferring data using a variety of predefined cipher and authentication combinations, called the SSL Record Protocol.
- On the upper layer, a protocol for initial authentication and transfer of encryption keys, called the SSL Handshake Protocol.
An SSL session is initiated as follows:
- On the client (browser), the user requests a document with a special URL that starts with https: instead of http: either by typing it into the URL input field, or by clicking the link. For example the major search engines like Google, Yahoo, Bing and other money transactions websites uses Secure Socket Layer (SSL).The client computers which do not installed the Secure Socket Layer (SSL) certificates on their computer unable to browse those sites.
- The client code recognizes the SSL request and establishes a connection through TCP port 443 to the SSL code on the server.
- The client then initiates the SSL handshake phase, using the SSL Record Protocol as a carrier. At this point, there is no encryption or integrity checking built into the connection.
The Secure Socket Layer (SSL) Protocol addresses the following security issues:
- Privacy: After the symmetric key is established in the initial handshake, the messages are encrypted using this key.
- Integrity: Messages contain a message authentication code (MAC) ensuring the message integrity.
- Authentication: During the handshake, the client authenticates the server using an asymmetric or public key. It can also be based on certificates. SSL requires that each message is encrypted and decrypted and therefore has a high performance and resource cost.
Secure Socket Layer (SSL) Protocol
The SSL protocol is located at the top of the transport layer. SSL is also a layered protocol itself. It simply takes the data from the application layer, re-formats it, and transmits it to the transport layer. SSL handles a message as follows.
The sender performs the following tasks
- Takes the message from upper layer.
- Fragments the data to manageable blocks.
- Optionally compress the data.
- Applies a message authentication code (MAC)
- Encrypts the data.
- Transmits the result to the lower layer.
The receiver performs the following tasks.
- Takes the data from lower layer.
- Decrypts.
- Verifies the data with the negotiated MAC key.
- Decompress the data if compression was used.
- Reassembles the message.
- Transmits the message to the upper layer.
An SSL session works in different states. These states are session and connection states. The SSL handshake protocol coordinates the states of the client and the server. In addition, there are read and write states defined to coordinate the encryption according to the change Cipher Spec messages.
Change Cipher Spec Protocol
The change Cipher Spec protocol is responsible for sending change Cipher Spec messages. At any time, the client can request to change current cryptographic parameters such as the handshake key exchange. Following the change Cipher Spec notification, the client sends a handshake key exchange and if available, certificate verify messages, and the server sends a change Cipher Spec message after processing the key exchange message. After that, the newly agreed keys will be used until the next change Cipher Spec request. The change Cipher Spec message is sent after the hello messages during the negotiation.
SSL handshake protocol
The SSL handshake protocol allows the client and server to determine the required parameters for and SSL connection such as protocol version, cryptographic algorithms, optional client or server authentication, and public key encryption methods to generate shared secrets. During this process, all handshake messages are forwarded to the SSL record layer to be encapsulated into special SSL messages. Figure below illustrates an SSL handshake process.
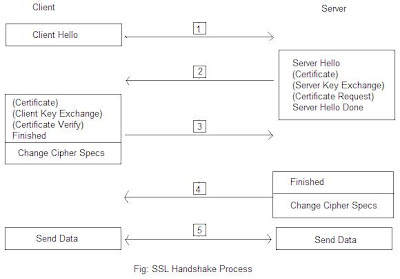
SSL record protocol
After the master key has been determined, the client and server can use it to encrypt application data. The SSL record protocol specifies a format for these messages in general, they include a message digest ensure that they have not been altered and the whole message is encrypted using a symmetric cipher.
Other Internet security methods are: Transport Layer Security (TSL), Pretty Good Privacy (PGP) and Firewall, I will post about them later. Keep following this blog.
You Might also view the following Related Posts
- Networking Fundamental
- Network Topology
- Network Functions
- Network Reference Models (Network Architectures)
- Internet Security & IP Security (IPSec)
- Secure Socket Layer (SSL)
